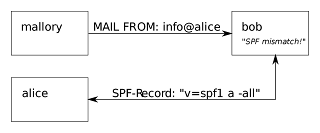
Sender Policy Framework (SPF) is a method of fighting
spam emails. SPF is designed to prevent forged or spoofed emails being sent by
checking and validating that the sender is authorised to send email from the domain
they're claiming to be from.
This is done by verifying the sender's email
server before delivering legitimate email to a recipient's inbox. That way, if
a spammer attempts to send email from a faked email address, the message will
be rejected.Sender Policy Framework (SPF) is an email authentication method designed to detect forged sender addresses in emails, (email spoofing), a technique often used in phishing and email spam.
SPF allows the receiver to check that an email claiming to come from a specific domain comes from an IP address authorized by that domain's administrators. The list of authorized sending hosts and IP addresses for a domain is published in the DNS records for that domain.
Wikipedia
The sender's address and other parts of the email header
are altered to appear as though the email originated from a different source.
It is a common method used by attackers to gain the trust of the target and
increase the likelihood of a successful attack. These emails often contain
malicious links or attachments which, when opened, can compromise networks.
Why Implement SPF
·
SPF can lower the chance of malicious content
reaching a network by providing protection against spoofed emails. SMTP without
SPF allows any computer to send email claiming to be from anyone so it is easy
for spammers to send email from forged addresses. This makes it very difficult
to trace back from which system Spam comes from. On the other hand it is very
easy for Spammers to fake their sender address so that the receiver trusts
these e-mails.
·
SPF allows an Administrator of an Internet
Domain to specify which machines are authorized to transmit e-mail from that
domain.
·
You can decide whether to block, quarantine or mark
incoming emails as suspicious/spam after failing SPF verification.
How to implement SPF
·
There are two sides to SPF; checking incoming
mail, and (publishing) allowing others to check the mail you send. You do the former by
using an SPF-enabled message transfer agent (MTA), and the latter by
registering an SPF record in DNS. SPF allows you to specify which servers are
allowed to send emails for your domain and makes this information available for
recipients to check. The SPF entry will contain a list of domains or valid IP
addresses authorised to send emails for their domain.
·
Identify SPF software compatible for your email
server. A list of software can be found at www.openspf.org/Implementations.
Microsoft Exchange server uses a type of SPF called "Sender ID".
·
Determine your organisation's SPF handling
procedure, preferably hard fail (blocking the messages at the gateway) instead
of soft fail (tagging the messages as spam but accepting them).
·
Define your outgoing mail servers and have an
SPF entry for this hostname. SPF records are usually laid out in typical DNS
syntax as follows:
“ v=spf1 mx a:mailserver.domain.com
-all
where:
o v=spf1
defines the version of SPF being used
o mx
specify your organisation’s authorised email servers
o a:
mailserver.domain.com machine that can send emails on behalf of your domain
o -all
specifies a hard fail, directing receivers to drop email sent from your domain
if the sending server is not authorised.
Note: If the policy chosen is to tag suspect emails
but deliver them to the intended recipient, this is done via ~all instead of
-all.
SPF Unsupported messaging systems
If a messaging system does not support SPF, it is possible
to place an SPF enabled MTA in front of your unsupported systems. The only
thing you have to do is to change the mail flow that all incoming mails will be
sent to the SPF aware MTA. This MTA checks the e-mail and will forward it to
the internal mail-system.
Note: SPF cannot detect cross-user forgery, that is, where
users within a given domain forge the email addresses of others.
image source